Service guidance
NoDDoS Infinite defense
In addition to responding to DDoS attacks through defense equipment, we are committed to protecting our customers' services with reliable services and differentiated technologies. We are analyzing the type of attack, not the frame-based defense policy, and we are achieving a more complete DDoS defense with rational response.
DDoS(Distributed Denial of Service) attack??
Malicious hackers infer the zombie PC (user computer) with malicious code and then use the zombie PC to create a large drain in traffic and server resources, resulting in an attack on the specific site (or IP).
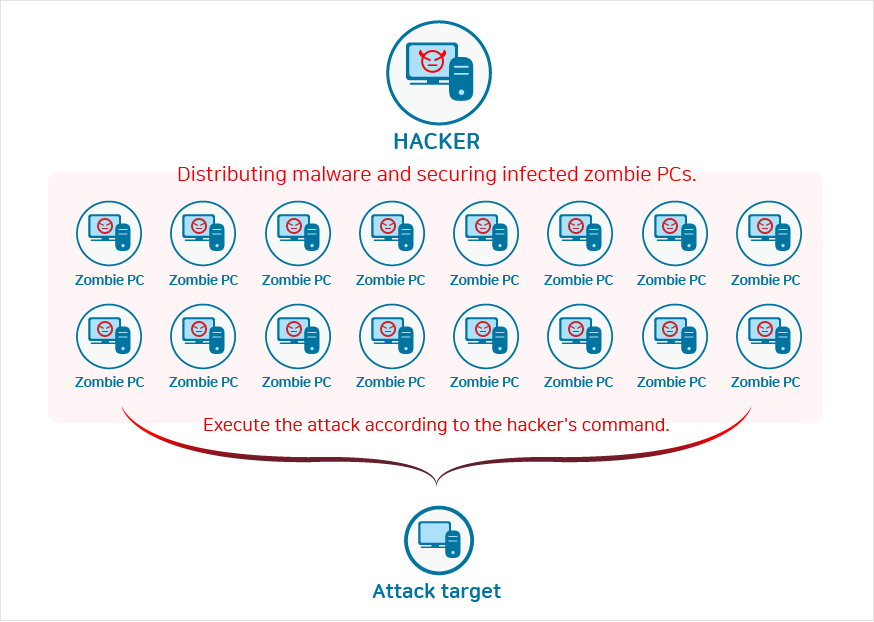
The reason this is intimidating is that it is not easy to defend against multiple simultaneous attacks by malicious code infected computers. Adult websites, chatting, games, and stock services were the main targets in the past, but more recently, there have been reckless attacks against all websites.Because there is no guarantee that an attack will stop or normalize, the best preparation is to implement a defense solution in advance.
Type of DDoS attack
| IP FLOODING | Compared to the TCP protocol, it is easy to reduce the packet size and send only the IP protocol indefinitely. |
| TCP attack |
- SYN Flood : Problems with the service by sending an excessive number of SYN connection requests to the service port. - FIN Flood : Constant occurrence of connections that produce normal connections and terminates immediately creating a normal connection to the TCP. - Fragment Flood : Request number of Fragment IP packets that are exceeded allowed - GET FLOODING:Many web services are connected to a large already or specific page and cause problems with the DB or service - String attack : An attack that paralyzes a service by including specific characters in the packet header in a service daemon port. - abnormal user-agents : attack by including agent values in packets that are not usable by normal clients other than the normal web browser - CC ATTACK : A webpage stores information about an open page into a client PC cache, in which case you can continue to request information from the server by attacking it for vulnerabilities. - TimeOut Connection : After a normal connection is requested, an ESTABLISHED is created and the service is not requested. |
| UDP attack | - Attack type that paralyzes the network by guessing what is going to be a gateway to the network - Block access from the outside to the gateway except for unauthenticated IP - Attacks that paralyze the network by sending UDP protocol in bulk |
| ICMP attack | - An attack that paralyzes the network by sending ICMP protocols in bulk |
NoDDoS - Defense service configuration diagram
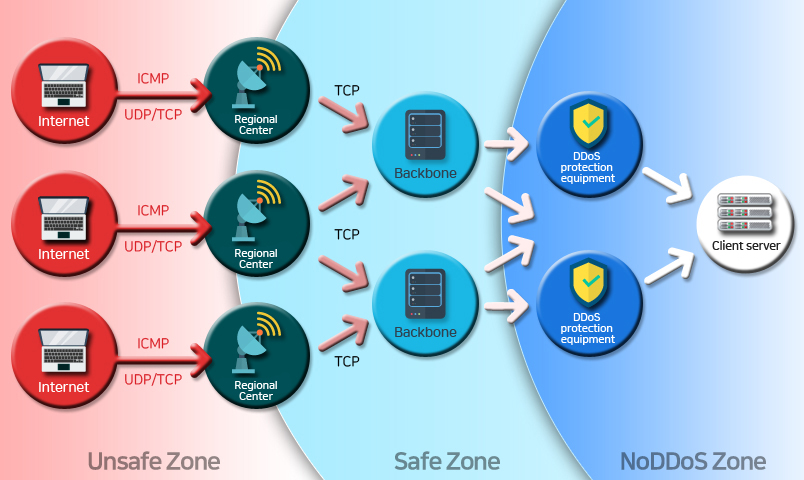
Three DDOS security zones are configured to block harmful traffic from network attacks such as UDP and ICMP in the regional network center when a DDoS attack occurs, and TCP defense from the backbone in the second place. Get Flood, CC Attack, and other web-load attacks.
In case of DDoS attack, real-time monitoring and notification are activated. At the same time, DDoS dedicated equipment is immediately shut down, so normal traffic flows into the actual customer's server and service is available 24 hours a day, 365 days a year.
NoDDoS Defense Service Features
ICMP,UDP Source blocking system, Backbone filtering 100G More than
Over 100G DDoS protection and attack blocking, UDP flood blocking, ICMP over attack protection is possible.
TCP 80G Defensible
New TCP,SYN,ACK,Non IPS,Row IPS,HTTP Get,CC and high-capacity attack defense / session and connection attacks against the ruleset is applied.
Defense Solution- 10G classUTM mounting
As the bandwidth of most institutional and large sites is expanding from 1G to 10G, it is costly and administrative difficult to cope with current network with existing 1G equipment. Therefore, to cope with this situation, NoDDoS has developed 10G security equipment to support more enhanced UTM solution.
Analysis of attack pattern and realization of defense system by real-time monitoring
Real-time monitoring to analyze and block DDoS attacks on attack packets, quick response to new pattern attacks, and establish a connection session defense system by limiting the number of connections per second per service port / host to block IP .
Direct retention and management of security equipment
For some DDoS defense companies, hosting is the main business, while DDoS defense is handed over to the defense equipment operator for management and management. NoDDoS is equipped with real defense equipment, and it manages operation and management directly by professional engineer, and can cope faster and more accurately when an attack occurs.
DDoS defense service comparison table
| division | NoDDoS | Third-party premium |
| Primary defense | Unlimited defenses (160G Multi UDP,ICMP) |
Null blocking when 60G is exceeded (UDP,ICMP) |
| Second defense | 80G Cluster Defense (IP and Port Individual type) |
10G Shared Type (TCP, etc.) |
| Attack Effect | none (Automatic defense / Multi pattern) |
Can be affected by attacks from other customers |
| Term of Agreement | 1 month prepaid | 3 months / prepayment |
| Installation cost | free | 300,000 won(\) / 1 time |
| Billing Criteria | Server Core Criteria No limit to the number of domains and ports | 1 server, 1 domain |
DDoS Attack Map
DDoS Attack Map is a real-time DDoS map provided by Google and Arbor Networks.


